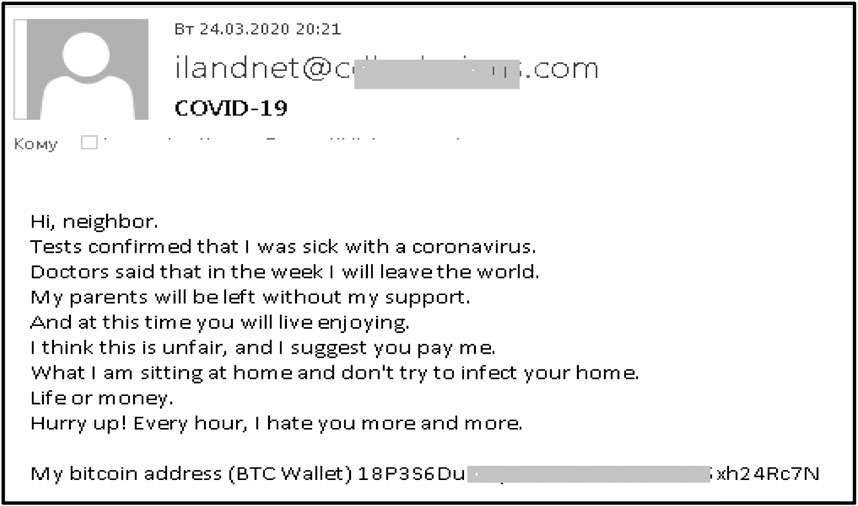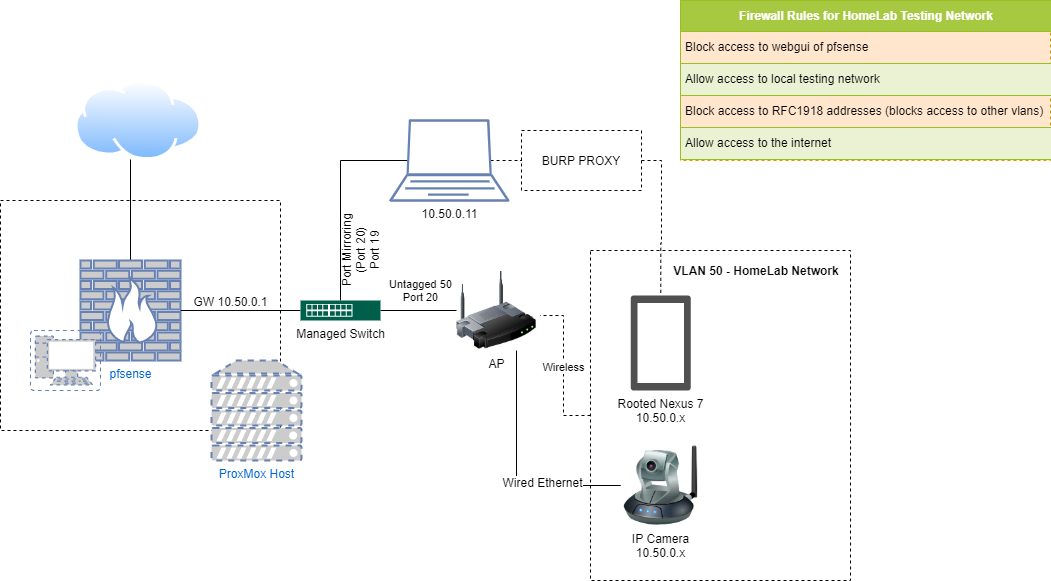
Lights, Camera, HACKED! An insight into the world of popular IP Cameras | NCC Group Research Blog | Making the world safer and more secure

Cybersecurity: Internet security 101: Six ways hackers can attack you and how to stay safe - The Economic Times
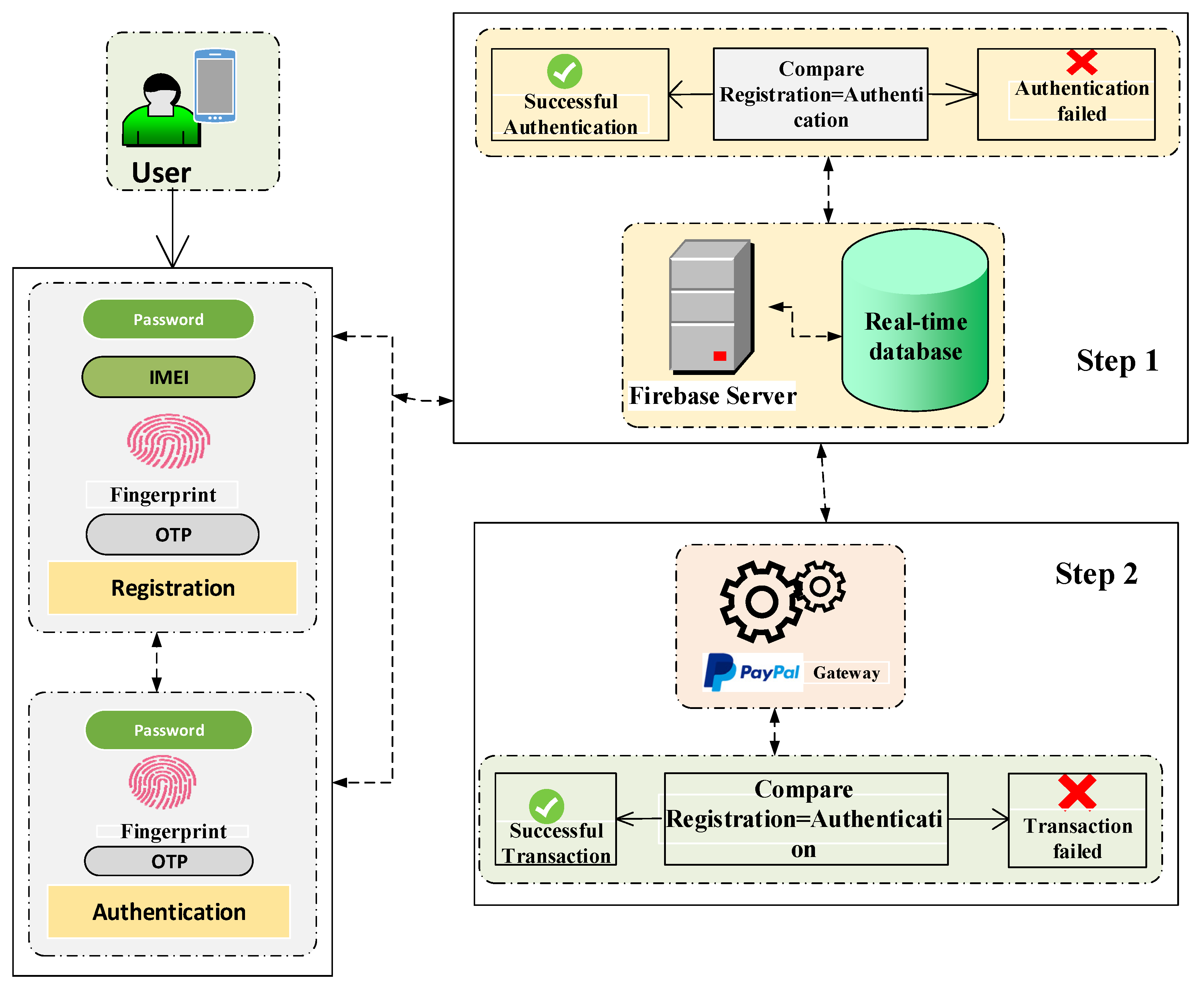
Electronics | Free Full-Text | Device Identity-Based User Authentication on Electronic Payment System for Secure E-Wallet Apps

The Art of Invisibility: The World's Most Famous Hacker Teaches You How to Be Safe in the Age of Big Brother and Big Data: Mitnick, Kevin, Vamosi, Robert, Hypponen, Mikko: 9780316380508: Amazon.com:

The Art of Invisibility: The World's Most Famous Hacker Teaches You How to Be Safe in the Age of Big Brother and Big Data: Mitnick, Kevin, Vamosi, Robert, Hypponen, Mikko: 9780316380508: Amazon.com:

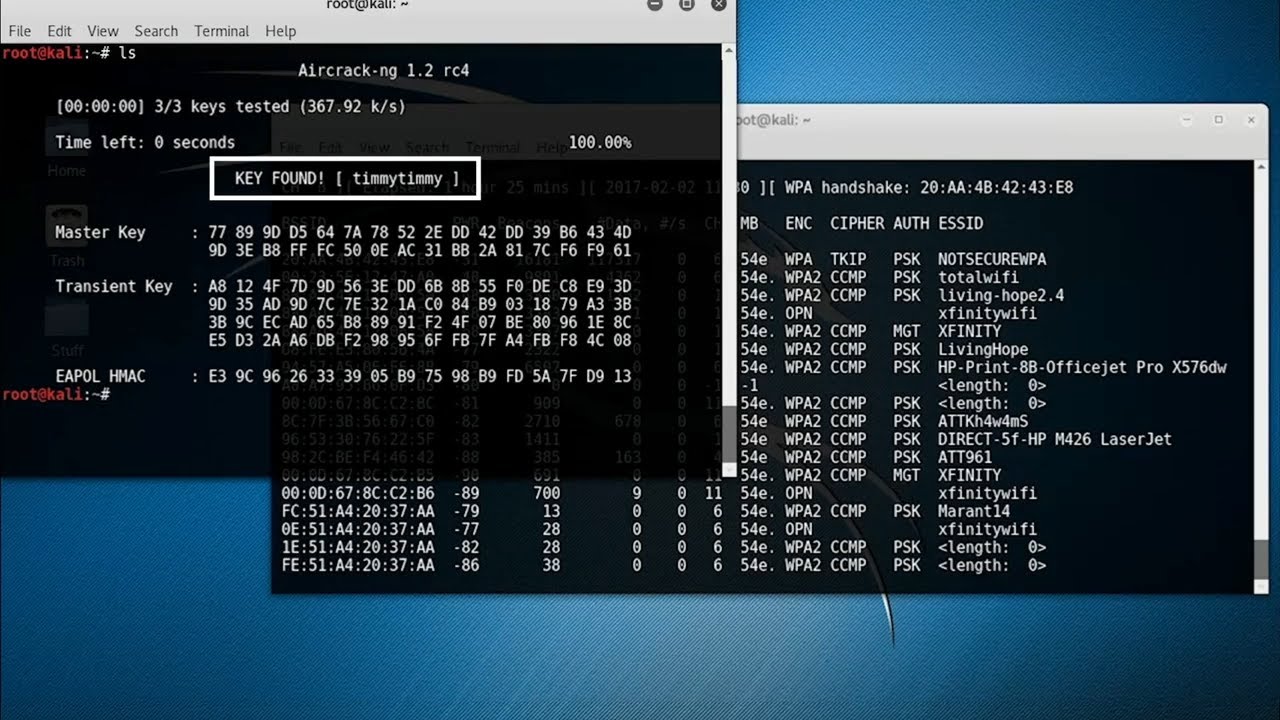








%20-%20refresh/The_Most_Dangerous_and_Famous_Hackers_Today-Hero-refresh.jpg)