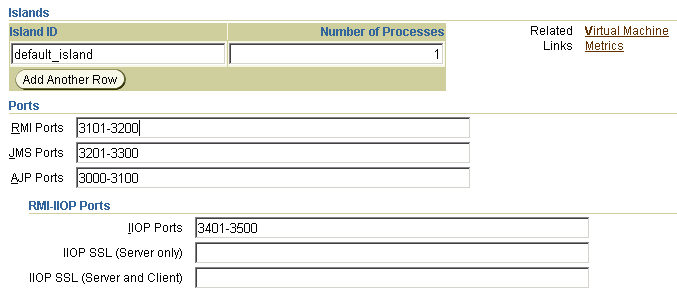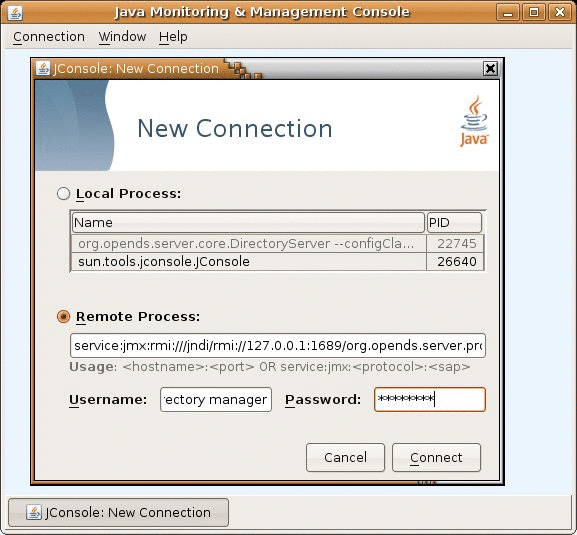
Accessing a Directory Server Instance From JConsole - Sun OpenDS Standard Edition 2.0 Administration Guide

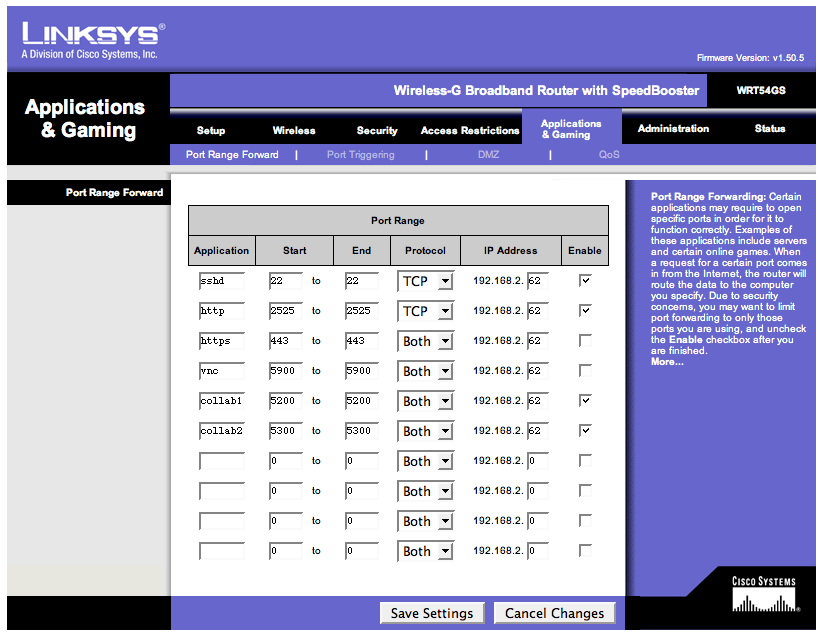
Port 1099 java rmi exploit | What is java rmi | Metasploitable 2 Vulnerable Machine Part 10 | Hindi - YouTube
BEA-150000 [Root exception is java.rmi.NoSuchObjectException: The object identified by: '31' could not be found - beawh - 博客园
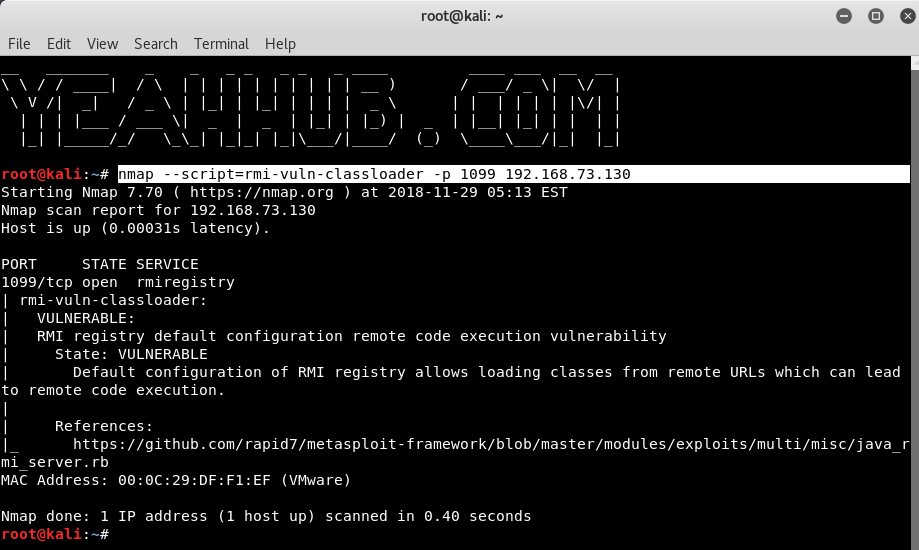
Java RMI Server Insecure Default Configuration Remote Code Execution Vulnerability' in Spectrum server
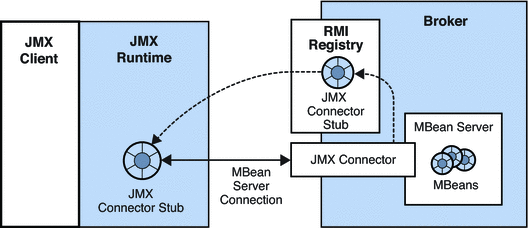
Java RMI for pentesters: structure, recon and communication (non-JMX Registries). | by AFINE | ITNEXT
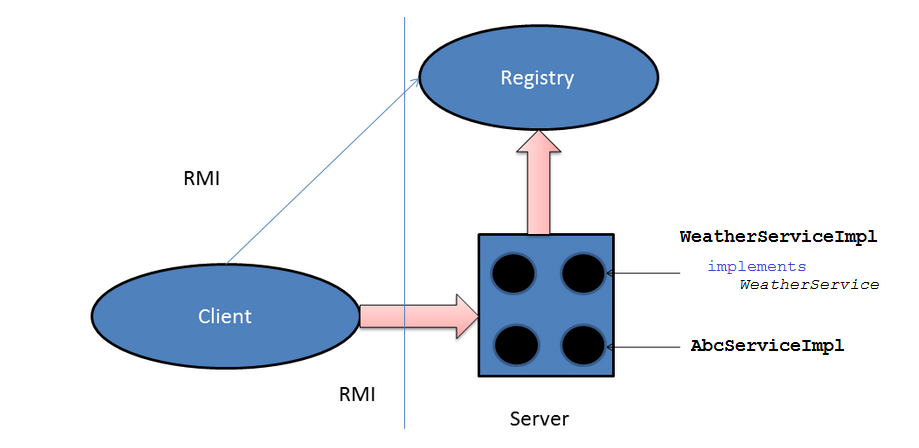
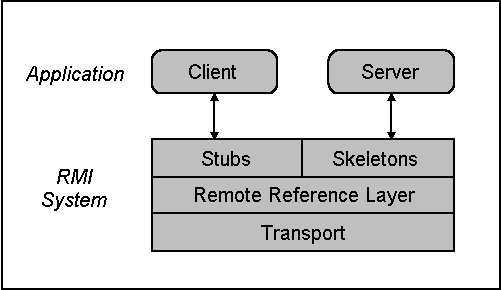
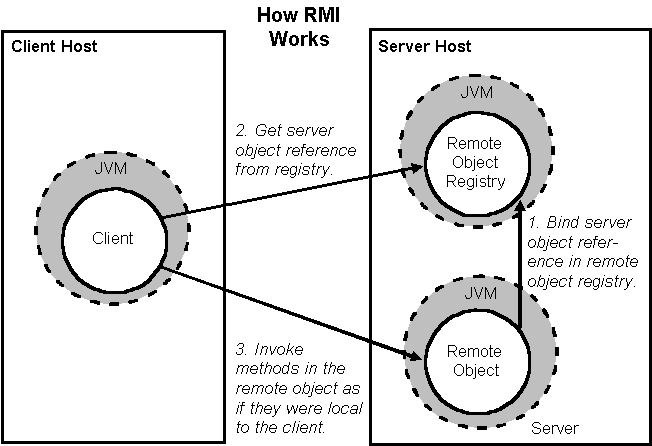
Java RMI RMI = Remote Method Invocation. Allows Java programs to invoke methods of remote objects. Only between Java programs. Several versions (JDK-1.1, - ppt download
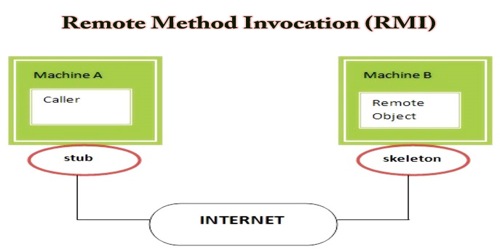
Java RMI for pentesters: structure, recon and communication (non-JMX Registries). | by AFINE | ITNEXT